Hi All
In this post, we will look at Open day light controller working with Juniper vMXs and how we can use the controller to get the BGP, BGP-LS and PCEP working. Once everything is up and running we will use the Controller to initiate the PCEP initiated MPLS LSPs between 2 VMXs.
Sounds interesting? Let’s see how we can achieve this.
Before I go further, if you want to check anything on PCEP and some of its concept, I did a post on Juniper Northstar Controller some time ago which you can check.
https://networkzblogger.com/2017/03/17/juniper-northstar-wan-sdn-controller/
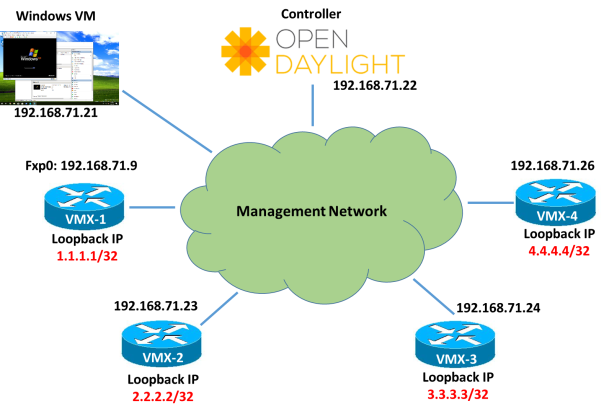
Below is the topology we will be using where all Juniper VMXs are loaded in Virtual Control Plane mode and they have fxp0 interface in 192.168.71.x subnet. Open day light controller version is Nitrogen and we have booted it on CentOS 7.5 version.
There is Windows VM in same subnet also from where we will run the REST APIs calls to Open day light using POSTMAN App.
We will divide the post into 3 parts.
- Configuring BGP/BGP-Link state between ODL and 192.168.71.24 VMX-3.
- Configuring PCEP session between all VMXs and ODL
- Initiate MPLS LSP from ODL using PCEP
I am assuming that you already know how to start an ODL controller. However if you don’t know let me know and I can help you.
So lets start with 1) Configuring BGP/BGP-Link state between ODL and 192.168.71.24 VMX-3.
If you already don’t know, Open day light versions in recent times doesn’t come auto-installed with all the features. You have to manually add them. You don’t need to download them individually. It’s just you need to activate them.
We will be configure the BGP and BGP-LS on VMX-3 first
Standard BGP config with IPv4 Unicast address family however for BGP-LS we have to enable a separate family traffic-engineering additionally.
root@VMX-3> show configuration protocols bgp
group opendaylight {
type internal;
description Controller;
local-address 192.168.71.24;
family inet {
unicast;
}
family traffic-engineering {
unicast;
}
peer-as 2856;
neighbor 192.168.71.22;
}
On ODL side, First install the BGP and restconf feature on karaf console using command
feature:install odl-restconf odl-bgpcep-bgp
Then using REST API we will enable the BGP Router-ID with Link State family
POST URL : 192.168.71.22:8181/restconf/config/openconfig-network-instance:network-instances/network-instance/global-bgp/openconfig-network-instance:protocols
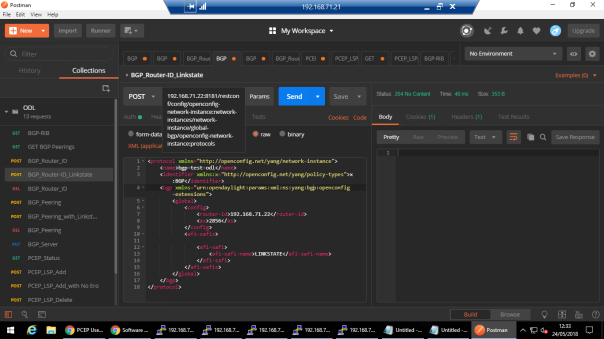
Then Configure the peer 192.168.71.24 with specific BGP Parameters and families
POST URL: 192.168.71.22:8181/restconf/config/openconfig-network-instance:network-instances/network-instance/global-bgp/openconfig-network-instance:protocols/protocol/openconfig-policy-types:BGP/bgp-test-odl/bgp/neighbors
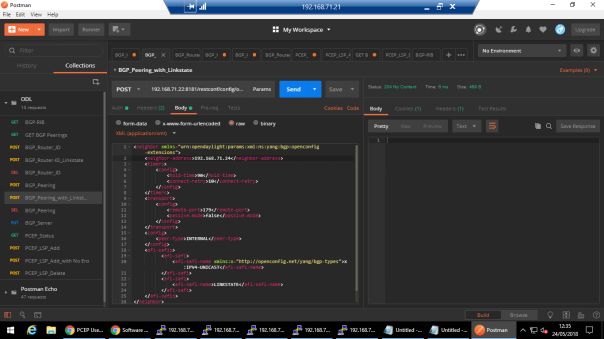
We can check the status of BGP peering off course from VMX side but let’s see what comes up from ODL side
GET URL: 192.168.71.22:8181/restconf/operational/bgp-rib:bgp-rib/rib/bgp-test-odl/peer/bgp:%2F%2F3.3.3.3
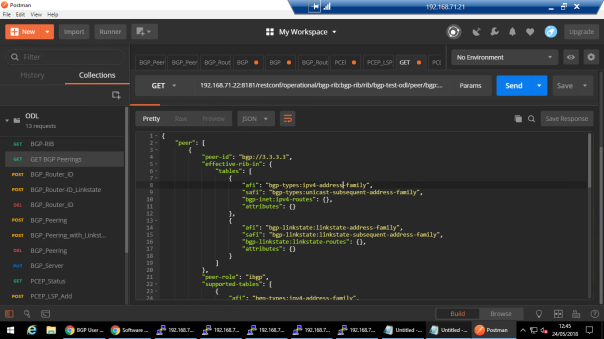
From VMX side:
root@VMX-3> show bgp neighbor Peer: 192.168.71.22+27755 AS 2856 Local: 192.168.71.24+179 AS 2856 Description: Controller Group: opendaylight Routing-Instance: master Forwarding routing-instance: master Type: Internal State: Established Flags: <Sync> Last State: OpenConfirm Last Event: RecvKeepAlive Last Error: None Options: <Preference LocalAddress LogUpDown AddressFamily PeerAS Refresh> Options: <VpnApplyExport DropPathAttributes> Address families configured: inet-unicast te-unicast Path-attributes dropped: 128 Local Address: 192.168.71.24 Holdtime: 90 Preference: 170 Number of flaps: 2 Last flap event: RecvNotify Error: 'Cease' Sent: 0 Recv: 33 Peer ID: 192.168.71.22 Local ID: 3.3.3.3 Active Holdtime: 90 Keepalive Interval: 30 Group index: 0 Peer index: 0 SNMP index: 0 I/O Session Thread: bgpio-0 State: Enabled BFD: disabled, down NLRI for restart configured on peer: inet-unicast te-unicast
BGP-LS configuration we did will be used to advertise the Traffic Engineering database to Controller. You can see the routes advertised using lsdist.0 table in juniper.
Snippet below:
root@VMX-3> show route table lsdist.0
lsdist.0: 11 destinations, 11 routes (11 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
NODE { AS:2856 Area:0.0.0.0 IPv4:2.2.2.2 OSPF:0 }/1152
*[OSPF/10] 02:02:38
Fictitious
NODE { AS:2856 Area:0.0.0.0 IPv4:3.3.3.3 OSPF:0 }/1152
*[OSPF/10] 02:02:43
Fictitious
NODE { AS:2856 Area:0.0.0.0 IPv4:4.4.4.4 OSPF:0 }/1152
*[OSPF/10] 02:02:38
Fictitious
NODE { AS:2856 Area:0.0.0.0 IPv4:4.4.4.4-192.168.71.26 OSPF:0 }/1152
*[OSPF/10] 02:02:31
Fictitious
LINK { Local { AS:2856 Area:0.0.0.0 IPv4:2.2.2.2 }.{ IPv4:192.168.71.23 } Remote { AS:2856 Area:0.0.0.0 IPv4:4.4.4.4-192.168.71.26 }.{ } OSPF:0 }/1152
*[OSPF/10] 02:02:31
Fictitious
..
…
…
2) Now let’s configure the PCEP
On VMX (This will be repeated on all with change in local address)
root@VMX-3> show configuration protocols pcep
pce odl {
local-address 192.168.71.24;
destination-ipv4-address 192.168.71.22;
destination-port 4189;
pce-type active stateful;
lsp-provisioning;
p2mp-lsp-report-capability;
}
If you have any firewall, make sure to allow port 4189 between Controller and VMXs.
On ODL, we need to install odl-bgpcep-pcep feature
There is no other config to do. As soon as you install this feature, you should see PCEP status up.
Let’s see it from VMX-4
root@VMX-4> show path-computation-client status
Session Type Provisioning Status
odl Stateful Active On Up
LSP Summary
Total number of LSPs : 0
Static LSPs : 0
Externally controlled LSPs : 0
Externally provisioned LSPs : 0/16000 (current/limit)
Orphaned LSPs : 0
odl (main)
Delegated : 0
Externally provisioned : 0
From ODL side:
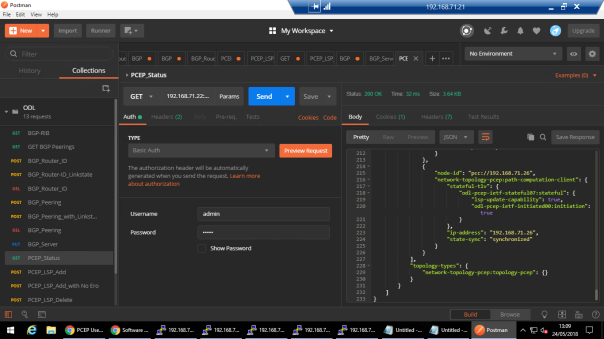
3) PCEP Initiated LSP
Now, we will configure the LSP from VMX-3 to VMX-4 between their Loopback IPs.
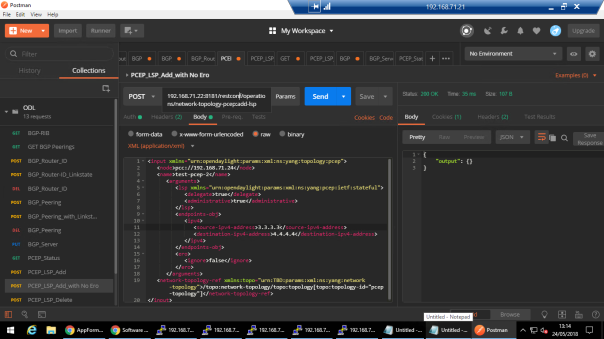
POST URL: 192.168.71.22:8181/restconf/operations/network-topology-pcep:add-lsp
You can see we haven’t given any ERO while provisioning the LSP. ODL has auto calculated the path and you can verify in VMX-3
root@VMX-3> show mpls lsp name test-pcep-2 extensive Ingress LSP: 1 sessions 4.4.4.4 From: 3.3.3.3, State: Up, ActiveRoute: 0, LSPname: test-pcep-2 ActivePath: (primary) LSPtype: Externally provisioned, Penultimate hop popping LSP Control Status: Externally controlled LoadBalance: Random Encoding type: Packet, Switching type: Packet, GPID: IPv4 LSP Self-ping Status : Enabled *Primary State: Up, Preference: 200 Priorities: 0 0 External Path CSPF Status: external SmartOptimizeTimer: 180 Flap Count: 0 MBB Count: 0 Received RRO (ProtectionFlag 1=Available 2=InUse 4=B/W 8=Node 10=SoftPreempt 20=Node-ID): 192.168.71.26(Label=0) 12 May 24 12:10:08.334 Self-ping ended successfully 11 May 24 12:10:07.830 EXTCTRL LSP: Sent Path computation request and LSP status 10 May 24 12:10:07.830 EXTCTRL_LSP: Computation request/lsp status contains: signalled bw 0 req BW 0 admin group(exclude 0 include any 0 include all 0) priority setup 0 hold 0 9 May 24 12:10:07.829 Selected as active path 8 May 24 12:10:07.828 EXTCTRL LSP: Sent Path computation request and LSP status 7 May 24 12:10:07.828 EXTCTRL_LSP: Computation request/lsp status contains: signalled bw 0 req BW 0 admin group(exclude 0 include any 0 include all 0) priority setup 0 hold 0 6 May 24 12:10:07.828 Up 5 May 24 12:10:07.828 Self-ping started 4 May 24 12:10:07.828 Self-ping enqueued 3 May 24 12:10:07.828 Record Route: 192.168.71.26(Label=0) 2 May 24 12:10:07.824 Originate Call 1 May 24 12:10:07.824 EXTCTRL_LSP: Received setup parameters :: Created: Thu May 24 12:10:07 2018 Total 1 displayed, Up 1, Down 0
You can do various operations like Deleting LSP, Modifying LSP etc from REST API.
One thing which we can’t do at the moment using PCEP is configuring Point to Multipoint LSP as standard is still being drafted for this but I hope it will come out soon.
So that’s all for now, I hope you enjoyed it and let me know your feedback.
Regards
Mohit