SONiC is an open source network operating system based on Linux that runs on switches from multiple vendors and ASICs. SONiC offers a full-suite of network functionality, like BGP and OSPF, VXLAN that has been production-hardened in the data centers of some of the largest cloud-service providers.
The community around SONiC has been growing and includes Juniper including Apstra, Arista, Nokia, Alibaba, Comcast, Cisco, Broadcom, Nvidia-Mellanox and VMware. SONiC underpins Microsoft’s Azure networking services. According to IDC, a SONiC data-center switch market will be worth $2 billion by 2024.
Some term it as ‘Linux of Networking’.
In this blog, we will see how to spin up a sample topology using vSONIC Virtual Switch on EVE-NG.
To start with, we will use mssonic.yml file which lists the generic parameters for spinning up the instance.
- Copy mssonic.yml file into “/opt/unetlab/html/templates/intel” or “/opt/unetlab/html/templates/amd” based on your cpu. In my case, I am using EVE-NG on macbook so I have used Intel.
root@eve-ng:~# ls -l /opt/unetlab/html/templates/intel/ | grep mssonic
-rw-r–r– 1 root root 1993 Jul 30 22:41 mssonic.yml
root@eve-ng:~#
2. Create a folder under “opt/unetlab/addons/qemu/” with name “mssonic-version/” like “mssonic-3.1.2”.
Keyword “mssonic” is important as using this only, eve-ng will recognize this image.
root@eve-ng:~# ls -l /opt/unetlab/addons/qemu/ | grep ms
drwxr-xr-x 2 root root 4096 Jul 30 22:48 mssonic-3.1.2
root@eve-ng:~#
https://github.com/Broadcom/sonic-VirtualSwitch/tree/master/3.1.2
3. Gunzip the .gz file to extract the image file.
root@eve-ng:/opt/unetlab/addons/qemu/mssonic-3.1.2# gunzip sonic-vs-3.1.2.img.gz
root@eve-ng:/opt/unetlab/addons/qemu/mssonic-3.1.2# ls -l
total 2380932
-rw-r–r– 1 root root 2438070272 Jul 30 22:55 sonic-vs-3.1.2.img
4. Rename sonic-vs-3.1.2.img to virtioa.qcow2. Please make sure to rename only and don’t convert it.
root@eve-ng:/opt/unetlab/addons/qemu/mssonic-3.1.2# mv sonic-vs-3.1.2.img virtioa.qcow2
root@eve-ng:/opt/unetlab/addons/qemu/mssonic-3.1.2# ls -l
total 2380932
-rw-r–r– 1 root root 2438070272 Jul 30 22:58 virtioa.qcow2
5. Fix the permissions as usual on eve-ng.
root@eve-ng:/opt/unetlab/addons/qemu/mssonic-3.1.2# /opt/unetlab/wrappers/unl_wrapper -a fixpermissions
root@eve-ng:/opt/unetlab/addons/qemu/mssonic-3.1.2#
Now we all set to use this under EVE-NG
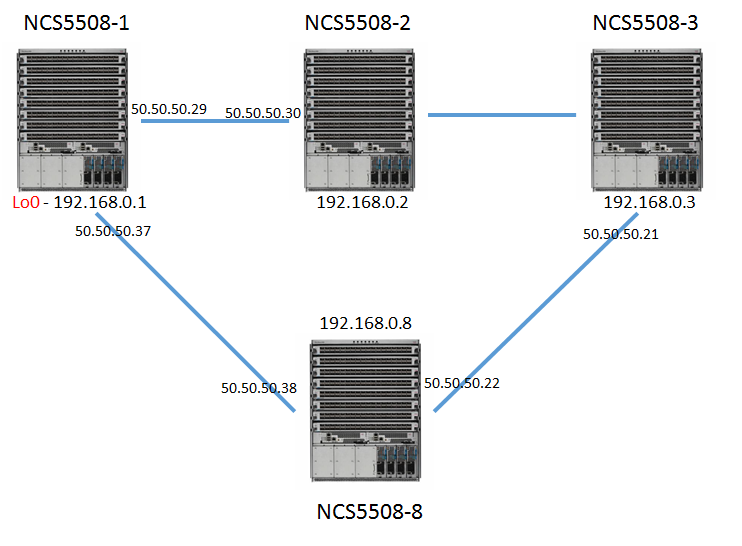
I have made a simple leaf-spine topology using Sonic Virtual Switches
6. Open the Eve-NG UI.
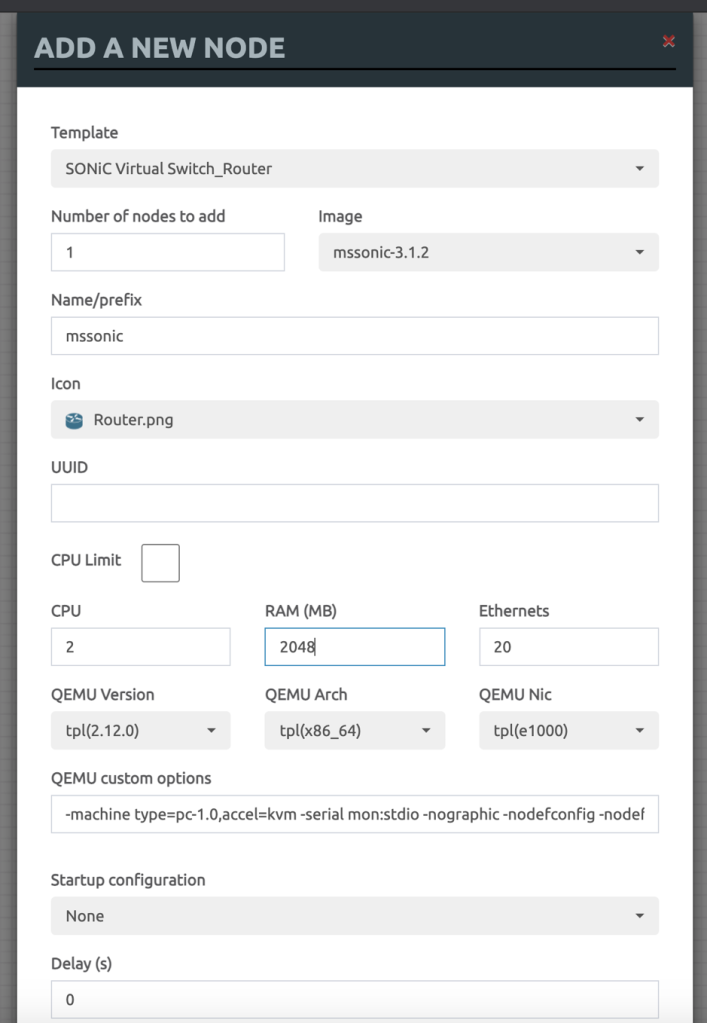
Add the new Node, and select Sonic Router as below.

7. Change any settings here if you need however defaults should be good.
8. I have built a simple Leaf-Spine topology using 4 Sonic VS.

9. Start one or more Switches and let it boot.
Trying 172.16.137.130…
Connected to 172.16.137.130.
Escape character is ‘^]’.
Jul 31 15:30:59.295935 2021 sonic INFO sonic-ztp[3850]: ZTP service started.
Jul 31 15:30:59.295971 2021 sonic INFO sonic-ztp[3850]: Failed to set system MAC address as the random number generator seed input.
Jul 31 15:30:59.295999 2021 sonic INFO sonic-ztp[3850]: Checking running configuration to load ZTP configuration profile.
Jul 31 15:30:59.893505 2021 sonic INFO sonic-ztp[3845]: Waiting for system online status before continuing ZTP. (This may take 30–120 seconds).
Debian GNU/Linux 9 sonic ttyS0
Jul 31 15:31:34.932822 System is ready
Jul 31 15:31:36.290136 2021 sonic INFO sonic-ztp[3845]: System is ready to respond.
Jul 31 15:31:36.308466 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet0
Jul 31 15:31:36.308525 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet1
Jul 31 15:31:36.308554 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet2
Jul 31 15:31:36.308581 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet3
Jul 31 15:31:36.308609 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet4
Jul 31 15:31:36.308637 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet5
Jul 31 15:31:36.308664 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet6
Jul 31 15:31:36.308741 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet7
Jul 31 15:31:36.308769 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet8
Jul 31 15:31:36.308821 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet9
Jul 31 15:31:36.308850 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet10
Jul 31 15:31:36.309163 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet11
Jul 31 15:31:36.340452 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet12
Jul 31 15:31:36.340489 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet13
Jul 31 15:31:36.340761 2021 sonic INFO sonic-ztp[3850]: Link up detected for interface Ethernet14
Default username/pwd – admin/YourPaSsWoRd
10. Once up and running, you would see lots of ztp related messages which can be disabled using below command.
sudo config ztp disable
sudo config save -y
11. Once done, you can go into sonic cli, using sonic-cli
admin@sonic:~$ sonic-cli
sonic#
sonic#
sonic# ?
clear Clear commands
configure Enter configuration mode
copy Perform file copy operations
exit Exit from the CLI
fast-reboot fast-reboot [options] (-h shows help)
image Image related commands
logger Enter messages into the system log
no No commands under Exec mode
ping Send ICMP ECHO_REQUEST to network hosts
ping6 Send ICMPv6 ECHO_REQUEST to network hosts
reboot reboot [options] (-h shows help)
renew Renew commands
show Show running system information
terminal Set terminal settings
tpcm SONiC image installation manager
traceroute Print the route packets take to the host
traceroute6 Print the route packets take to the IPv6 host
warm-reboot warm-reboot [options] (-h shows help)
write Save config
sonic#
to prove its working, lets configure IP Addresses on Interfaces and see if we can ping each other.
On Leaf-1:
sonic(config)# hostname leaf-1
leaf-1#
leaf-1#
leaf-1#
leaf-1#
leaf-1# show running-configuration interface Ethernet 0
!
interface Ethernet0
mtu 9100
speed 25000
fec none
no shutdown
ip address 10.10.10.2/30
leaf-1#
On Spine-1:
spine-1# show running-configuration interface Ethernet0
!
interface Ethernet0
mtu 9100
speed 25000
fec none
no shutdown
ip address 10.10.10.1/30
spine-1#
12. Ping the other end to find everything is working
spine-1# ping 10.10.10.2
PING 10.10.10.2 (10.10.10.2) 56(84) bytes of data.
64 bytes from 10.10.10.2: icmp_seq=1 ttl=64 time=5.32 ms
64 bytes from 10.10.10.2: icmp_seq=2 ttl=64 time=1.34 ms
^C
— 10.10.10.2 ping statistics —
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 1.349/3.336/5.323/1.987 ms
spine-1#
That’s all, hope you like it.. In next sessions, we can go through some more specific scenarios around it.